LAS VEGAS--A researcher said today that he has discovered a number of vulnerabilities in programmable logic controllers (PLCs) from Siemens that are used to automate mechanical devices in utilities, power plants, and other industrial control environments and which could be remotely controlled to cause damage if connected to the Internet.
Dillon Beresford, a security researcher at NSS Labs, conducted demos of some attacks on the various Siemens Simatic Step 7 systems during his presentation at the Black Hat security conference here.
Beresford's work shows that it's possible to read and write data to a PLC memory even when password protection is enabled, retrieve sensitive information from the PLC, capture passwords, execute arbitrary commands, report false data back to the operator and lock the operator out of the PLC by changing the password, as well as completely disable the PLC, among other things, he said.
Attacks could be "wormed" and designed to spread to engineers' workstations or hop from system to system, Beresford said. "You can pretty much own everything on the automation network," he added.
In the long run, an attacker could damage equipment or make devices in the field explode or spin out of control, depending on what actions are taken, according to Beresford. "These capabilities have been used offensively before and they have caused things to explode," he said.
The problems were serious enough to prompt NERC (North American Electric Reliability Corp.) to release an alert just to utilities last night with mitigation information, but at the lowest level of alert, said Tim Roxey, director of Electric Sector Information Sharing and Analysis Center at NERC.
Separately, NERC released a public alert to warn utilities about findings of Don Bailey, senior security consultant at iSec Partners, who gave a presentation earlier in the day at Black Hat about telephony-based weaknesses related to PLCs. The vulnerabilities allowed him to unlock a car with a text message and also affect critical infrastructure environments.
These problems are worldwide. "It's not just the U.S. but around the globe," Roxey said during a news conference later in the day.
Although he focused on Siemens in his research and hardcoded passwords that create what he described as a "back door" to the PLC, attacks could be executed against systems from other vendors, Beresford said.
Part of the problem is that PLC protocols were designed without factoring in security. The protocol was intended to be open and packets are sent in plain text, he said, echoing concerns voiced by Jonathan Pollet, founder of Red Tiger Security, and Tom Parker, chief technology officer of FusionX, in their SCADA security workshop earlier in the week. "We need better access controls in PLCs," Beresford said. "That's something I believe Siemens is working on now."
Specifically, he was able to decrypt the hardcoded password in the system, which was "basisk"--which means "basic" in German--and create a command shell to dump memory in the PLC, look at the source code, execute commands, and intercept communications to and from the PLC, he said.
Such attacks are not really that difficult to pull off, with the right equipment, know-how, and ambition, he said. Experts speculated that last year's Stuxnet threat, which targeted Siemens Simatic Step 7 systems, was created by a nation-state or nation-state partners to sabotage Iran's nuclear development program. But, "single guys sitting in their basements could pull this off," he said.
Meanwhile, Beresford said that he also found what is known as an "easter egg," or hidden joke, in the Siemens code in the form of dancing monkeys and a German proverb that roughly translates to "all work and no play makes Jack a dull boy," he said, wearing a shirt with monkeys on it given to him by someone at Siemens.
Siemens is working to address the security issues that have cropped up, and ICS-CERT is working on an advisory, Beresford said.
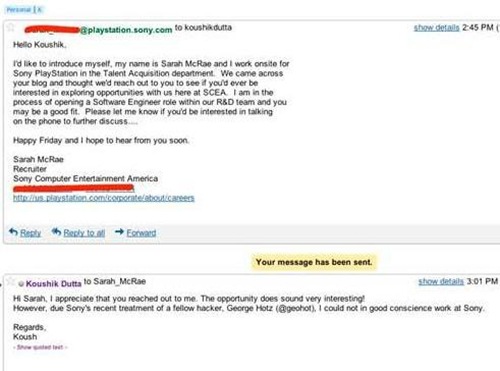
Beresford introduced Thomas Brandstetter, a CERT program manager for Siemens, during his presentation and said of Siemens, "I give them a lot of credit for not trying to pull my talk." (Beresford canceled his talk on Siemens vulnerabilities at the last minute at a conference in May after U.S. cybersecurity and Siemens officials expressed concerns that fixes weren't ready.)
"At some point you really have to accept that there are vulnerabilities in your products, and even monkeys," Brandstetter, who was also wearing a monkey shirt, said to laughs from the audience. "Accepting this was the first step in order to be able to handle this professionally."
"What he's done is open up a can of worms that we've [researchers] known for a long time," Pollet of Red Tiger Security said in the news conference. "There's a systemic problem across all vendors around authentication for (SCADA communication) sessions."
"This type of an attack could cause regional impact on one plant or others in the regional area," and there could be cascading outages, Pollet said.
























 www.best4hackingnews.blogspot.com
www.best4hackingnews.blogspot.com



 When it comes to hacking, every other guy tends to tape the "hacker" word with his name/codename without even realizing its significance. Then there is Facebook ...Have a look at it -
When it comes to hacking, every other guy tends to tape the "hacker" word with his name/codename without even realizing its significance. Then there is Facebook ...Have a look at it -